System Logs
System Logs record information on activities done in the application, such under Admin, Purchases, CMDB, Custom Module, etc. In addition to these, user addition, deletion, updates, and mail configuration are also recorded.
Role Required: SDAdmin
To access system logs,
- Go to Setup > Data Administration > System Log.
- From the system logs list view, click on any specific log to view the details.
Delete Logs
To delete logs individual or multiple, select the log(s) using the check boxes and click Delete at the top. You can also click Delete All to delete all the log files at once.
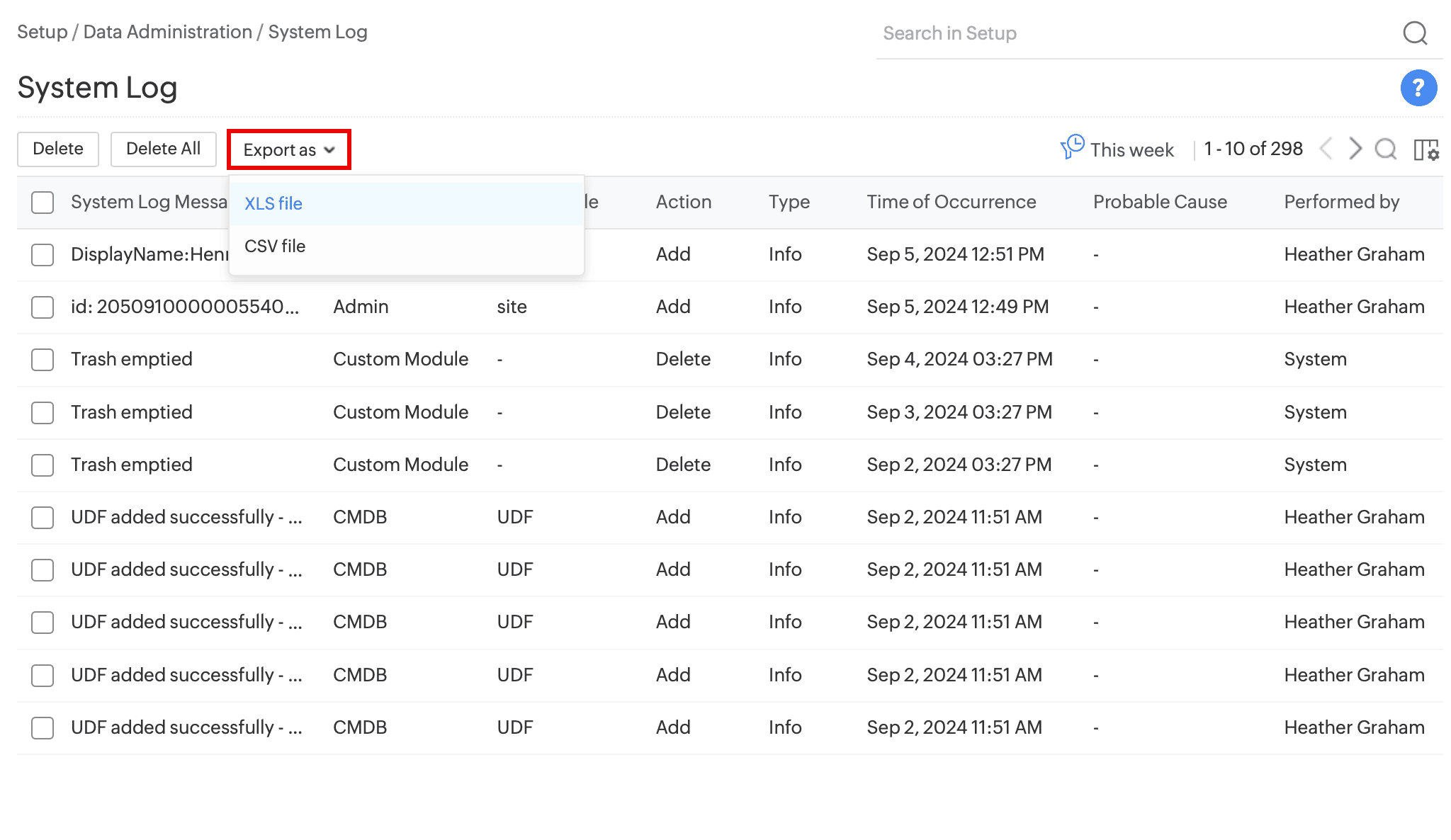
Export Logs
You can export system logs as a CSV or XLS file. Click on the Export as button at the top to export the log files.
Related Articles
PII/ePHI Logs
PII/ePHI logs record actions performed on Personally Identifiable Information (PII) and electronic Protected Health Information (ePHI), including the user's name, social security number, racial/ethnic data, etc. Role Required: SDAdmin The PII/ePHI ...Privacy Settings
General Data Protection Regulation (GDPR) protects all types of personally identifiable information (PII) and electronic Protected Health Information (ePHI), including users' names, social security numbers, insurance details, and racial or ethnic ...User Profile
Update Profile Picture Click the profile icon and hover over the profile picture to update it. The picture can be in JPG, PNG, JPEG, and BMP formats. Note that the file size should not exceed 5MB. Personalize Customize your display language, time, ...Asset FAQs
Asset Management License Consumption and Asset States Will an asset be included in license consumption if it is moved to a disposed or expired state? No, Disposed or Expired assets do not consume license. How to create an asset state similar to ...Audit Log
Audit Logs record all operations that an admin does under Setup. When there are multiple administrators, audit logs provide information on who, what, when, and where an action was performed. Audit log entries cannot be edited/deleted. Audit logs ...